AI Powered Application Security Posture Management
Tromzo’s AI-powered platform helps security teams prioritize and remediate the risks that matter. By leveraging deep code context and reachability analysis, Tromzo ensures highly accurate triage and remediation outcomes, eliminating noise and focusing on vulnerabilities that truly impact your organization.
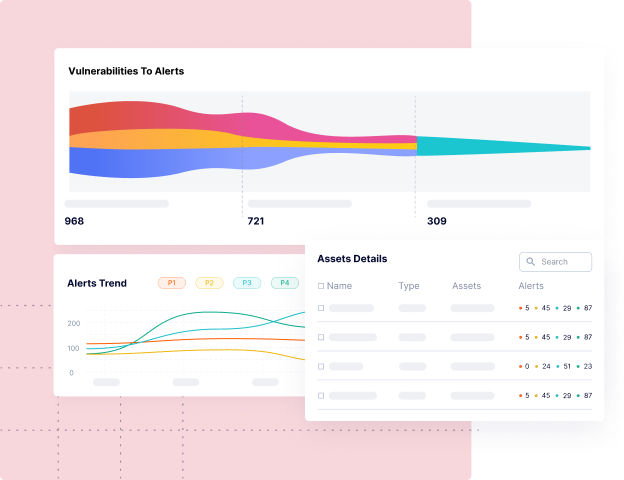
Unified Security Data Lake
Centralize security findings from all sources—SAST, DAST, SCA, CSPM, CNAPP and more—creating a comprehensive security posture of all your business applications, across code to cloud.
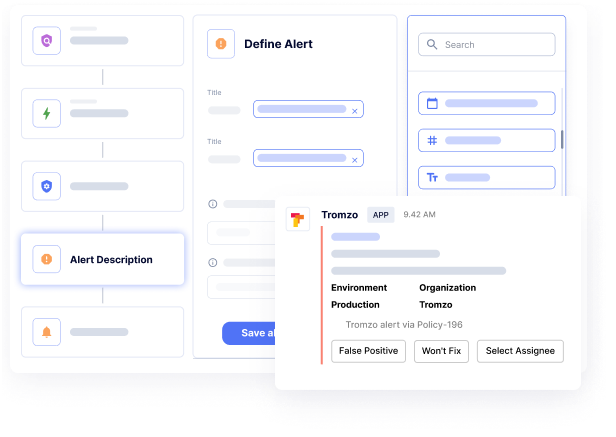
AI-Powered Risk Prioritization and Triage
Tromzo’s AI agents autonomously validate vulnerabilities, determine true risk impact, and eliminate false positives—automating the most manual and critical work in vulnerability management. By leveraging deep code analysis to assess reachability and exploitability, our agents ensure highly accurate triage and prioritization of vulnerabilities from all of your existing scanners.
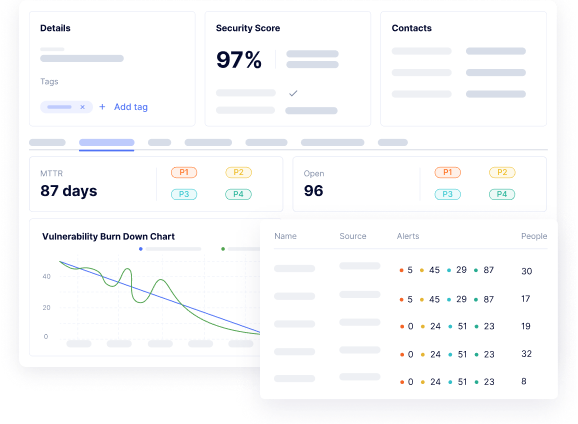
Comprehensive Security Posture Reporting
Get clear, actionable insights into your security program with tailored, compliance-ready dashboards. Tromzo provides in-depth reporting on the real risk posture of every business application, enabling you to track risk reduction and demonstrate measurable progress over time.
Common Use Cases
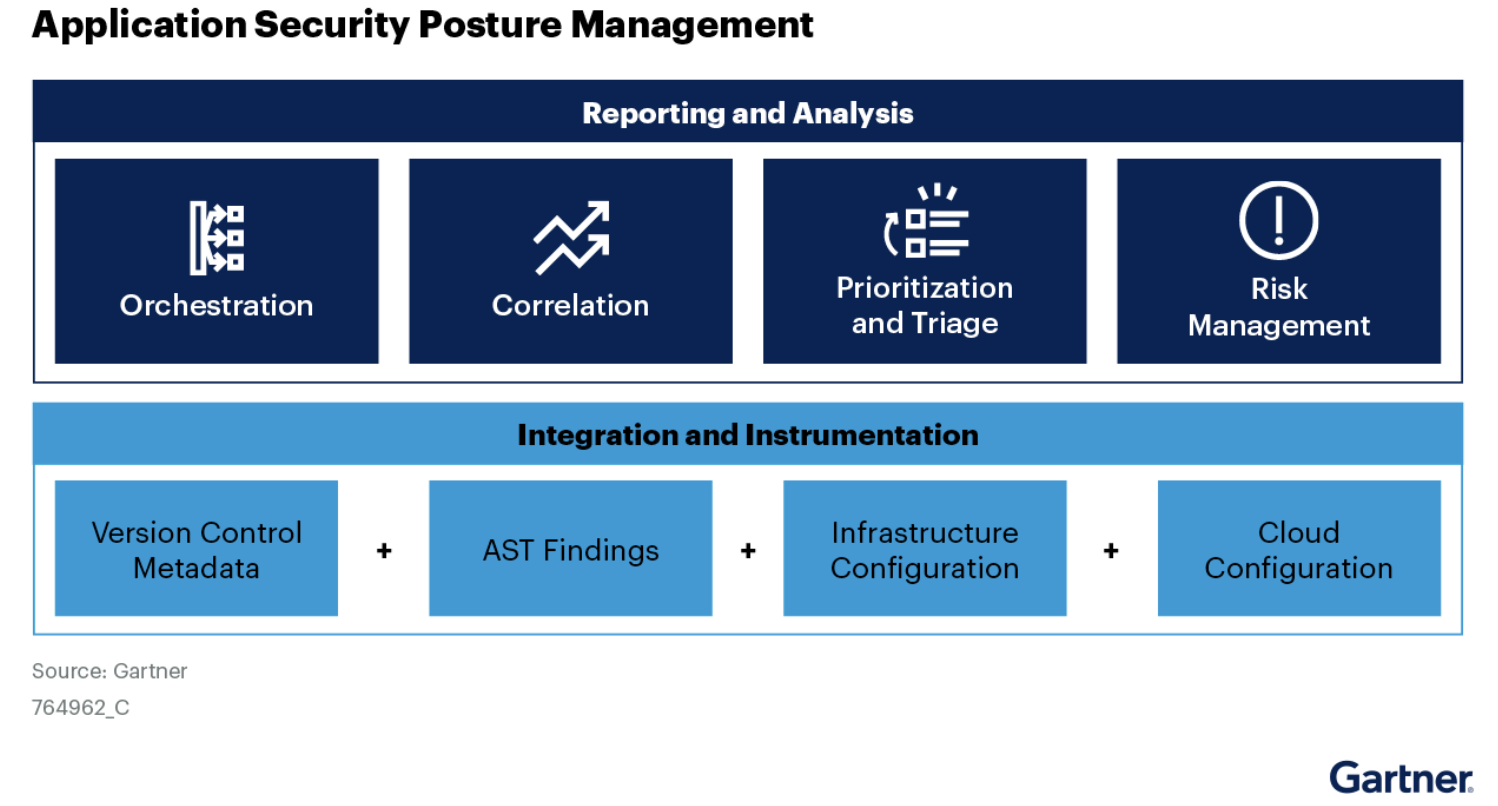

Application Security Posture Management
Tromzo enables security teams to act on the risks that matter. Using a security data lake and AI-powered agents, we automate triage and prioritization of vulnerabilities from all your scanners for fast remediation. Tailored reporting and actionable analytics help track progress and align with your security and risk goals.

Application Security Orchestration Correlation
Tromzo enables organizations that are looking to tackle ASOC – with code to cloud visibility and the ability correlate these findings for prioritization of critical remediation efforts, our customers move to automated vulnerability remediation and data driven security programs.
ASOC Buyer’s GuideRisk Based Vulnerability Management
When looking to build a successful vulnerability management program, leading organizations have leveraged Tromzo’s Intelligence Graph to implement advanced prioritization techniques and automated workflows with the solid foundation of software asset inventory, ownership, and business context.
Tackling aggregation & deduplication, contextual prioritization, automated workflows, and comprehensive dashboards.
The Key to Achieving Effective Vulnerability RemediationSoftware Supply Chain Security
Tromzo enables organizations to protect their software supply chain through:
Visibility of internal and external code with strong version-control policies, using artifact repositories for trusted content, and managing vendor risk throughout the delivery life cycle.
Hardening of the software delivery pipeline by configuring security controls in CI/CD tools, securing secrets and signing code and container images.
And, securing the operating environment via policies for governing access to resources using principles of least privilege and a zero-trust security model.
Risk-Based Application Security Management Platform
Contextualized Data. Security Guardrails. Automated Workflows.
Tromzo is a unified platform to incorporate security throughout the modern SDLC.
Security Teams That Trust Tromzo


















Backed by Leading CISOs
Tromzo was created to make security accessible, easy, and natural for developers while improving security throughout the software development lifecycle.
More than 25 CISOs saw how essential Tromzo is for modern application and product security teams, so they personally invested in Tromzo so we could bring our Product Security Operating Platform to market.
Backed by Leading CISOs
Backed by 25+ leading CISOs. Built by security practitioners to make security accessible, easy, and natural for developers while improving security throughout the software development lifecycle.


















Backed by Leading CISOs
Tromzo was created to make security accessible, easy, and natural for developers while improving security throughout the software development lifecycle.
More than 25 CISOs saw how essential Tromzo is for modern application and product security teams, so they personally invested in Tromzo so we could bring our Product Security Operating Platform to market.
Ready to Scale Your Application Security Program?
Sign up for a personalized one-on-one walkthrough.