DevSecOps-First ASOC
Built for development, platform engineering, cloud operations & security teams
Tromzo provides organizations with code to cloud context and visualization of the SDLC process for frictionless application security via security policy orchestration and software delivery data correlation.
Discover Artifact Inventory & Risk Posture
Contextual software asset inventory (code repos, software dependencies, SBOMs, containers, microservices, etc.), so you know what you have, who owns them, and which ones are important to the business.
Drive Real Vulnerability Remediation at Scale
Leverage context from Intelligence Graph to tune out the noise and automate the remediation lifecycle, so you can eliminate the manual processes of triaging, prioritizing, associating ownership, risk acceptance, and compliance workflows.
Achieve a Data Driven Security Program
Understand the security posture for every team with SLA compliance, MTTR, and other custom KPIs, so you can drive risk remediation and accountability across the organization.
How Do We Do All This? – Intelligence Graph
Prioritize remediation of vulnerable dependencies that have an exploit available. Deduplicate thousands of vulnerabilities in production hosts and containers.
Automatically identify which code repositories are processing PCI/PII/TIN relevant information.
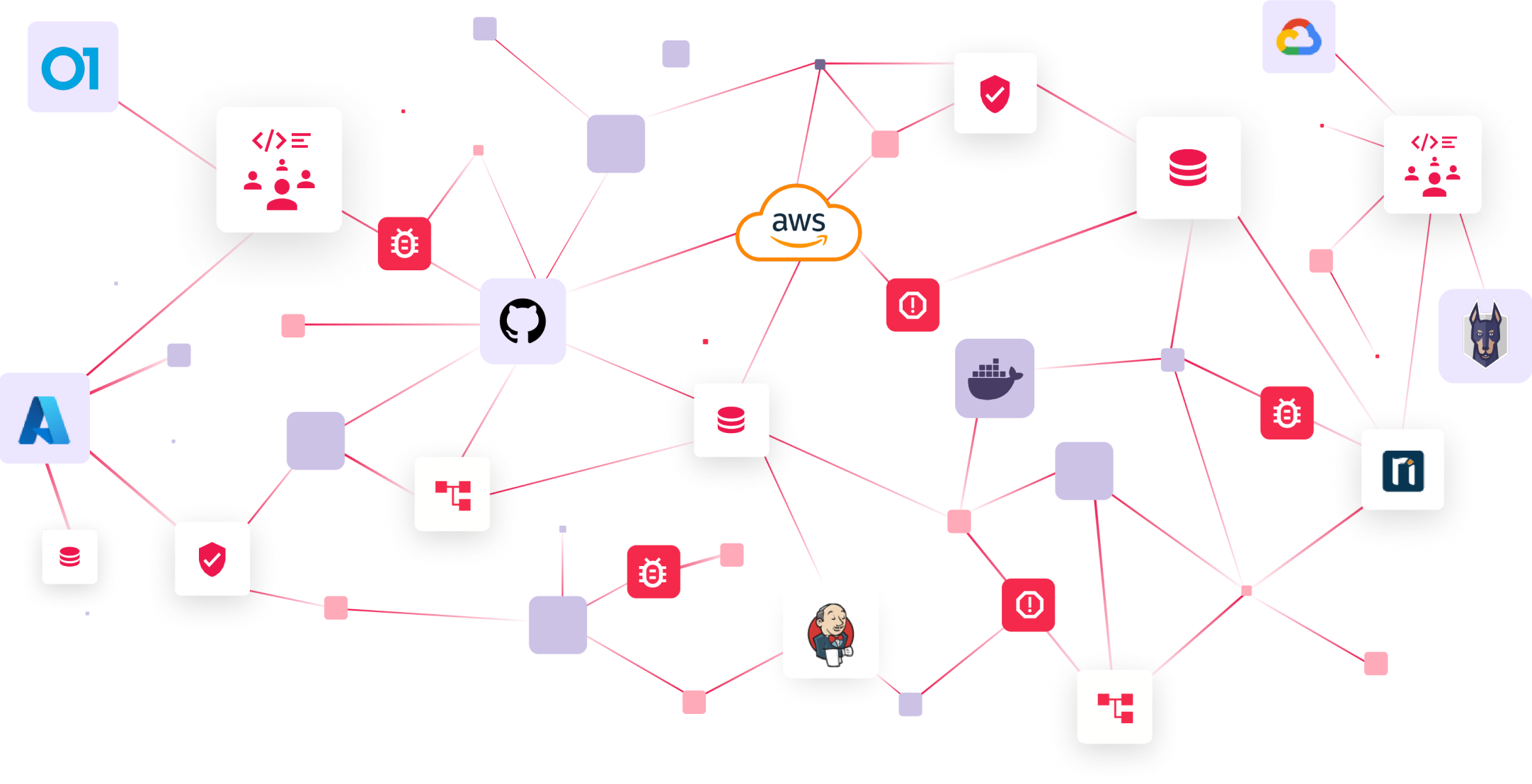
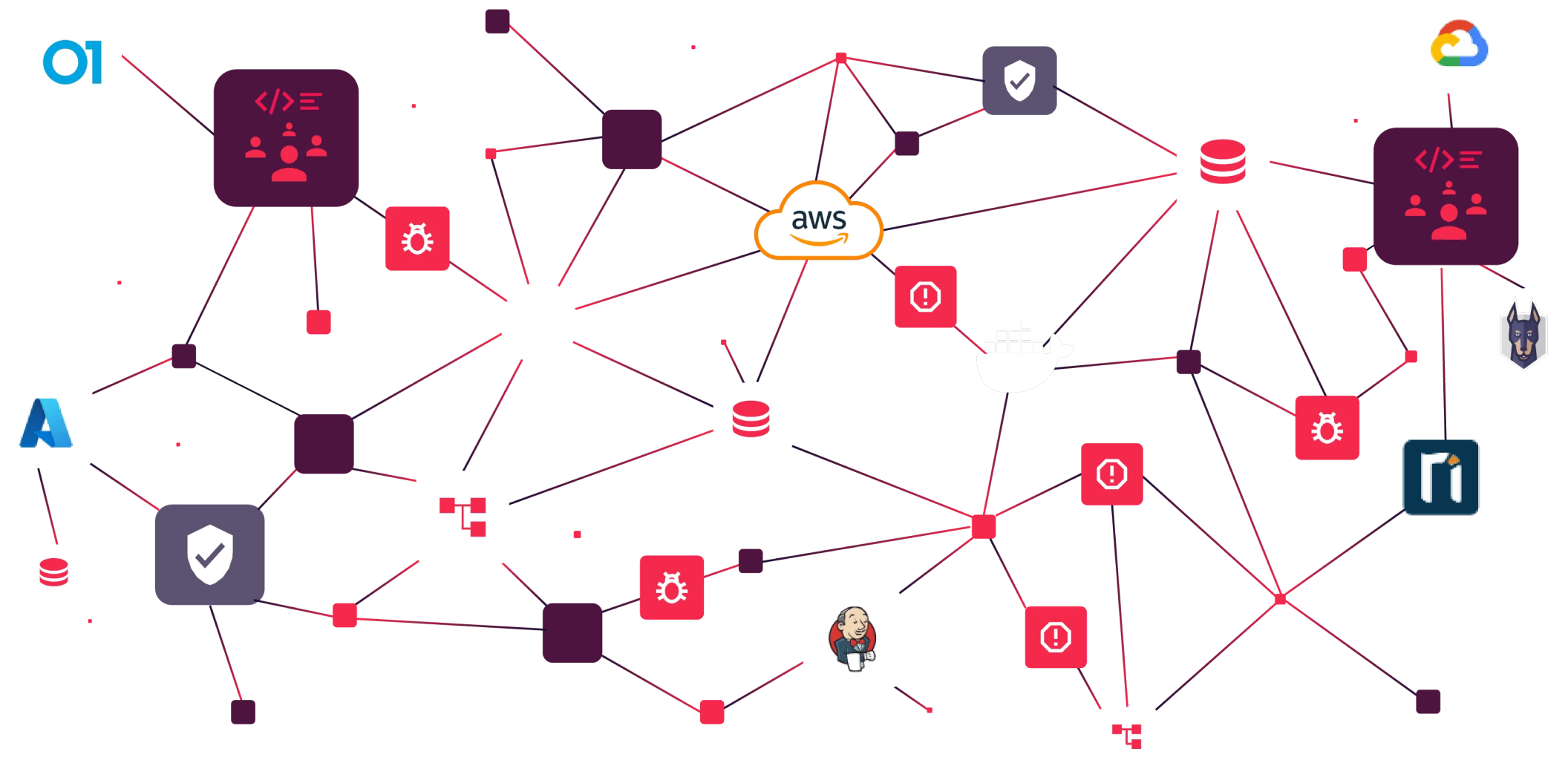
The Benefits of Effective ASOC
Tromzo’s Application Security Orchestration and Correlation (ASOC) solution continuously manages organizational risk by detecting, correlating, and prioritizing security issues across the SDLC – from code to cloud. We ingest data from a myriad of sources, enabling comprehensive analysis and correlation, resulting in deep environmental and organizational contextual insights for efficient triaging and remediation. Additionally, as a management and orchestration layer, Tromzo empowers organizations to effortlessly implement and enforce security policies, while seamlessly integrating with application and cloud security tools.
Risk-Based Application Security Management Platform
Contextualized Data. Security Guardrails. Automated Workflows.
Tromzo is a unified platform to incorporate security throughout the modern SDLC.
Recent articles in our Blog
On a recent episode of the Future of Application Security podcast, Chad Girouard, AVP Application Security at LPL Financial, talked about some of the challenges to overcome...
On a recent episode of the Future of Application Security podcast, Dave Ferguson, Director of Technical Product Management, Software Supply Chain Security at ReversingLabs, explained why the...
Ready to Scale Your Application Security Program?
Sign up for a personalized one-on-one walkthrough.