KPIs to Reduce Risk & Build Effective Security Programs
Measuring security effectiveness is hard. However, using KPIs is the only way to measure and improve a security program’s effectiveness and maturity. Reporting the right KPIs to the right audience not only helps with risk reduction, but also improves security culture by driving ownership and accountability of security.
Comprehensive Visibility
In-depth visibility across your organization, from individual teams to the entire development organization.
Asset visibility from applications to infrastructure (code repos, software dependencies, SBOMs, containers, microservices, etc.).
Out-of-the-box metrics for SLA compliance, MTTR, burn down rates, etc.
Tailored
Dashboards
Out-of-the-box dashboards with drag-and-drop widgets.
Autogenerate custom dashboards for quick views on SLAs, KPIs, MTTR, etc.
Build new views with no coding required.
Custom Visualizations
Highlight critical KPIs, SLAs, and custom metrics directly in your dashboards.
Automatically graph any data with Tromzo’s intelligence graph, alerts, vulnerabilities, missing controls, risk ownership, and more.
Shareable Dashboards
Drive decisions via data and share relevant dashboards with anyone in your organization.
Generate custom dashboards to provide real-time views to external teams.
How Tromzo Can Help
Tromzo’s unified Product Security Operating Platform (PSOP) brings security visibility and control to the entire software lifecycle from code to cloud, so your organization can build secure software, fast!
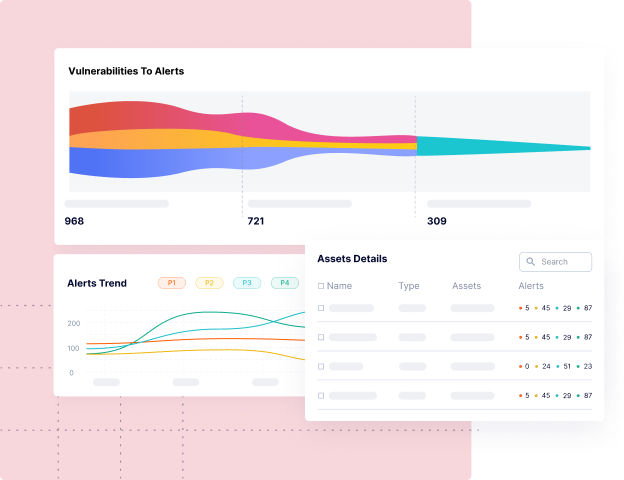
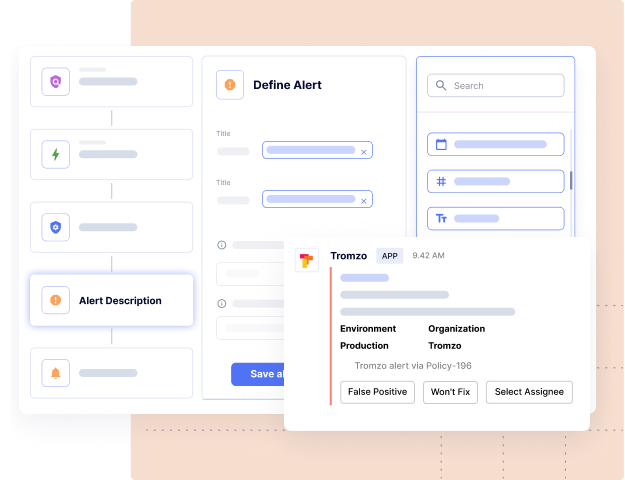

Discover Artifact Inventory & Risk Posture
Contextual software asset inventory (code repos, software dependencies, SBOMs, containers, microservices, etc.), so you know what you have, who owns them, and which ones are important to the business.
Drive Real Vulnerability Remediation at Scale
Leverage context from Intelligence Graph to tune out the noise and automate the remediation lifecycle, so you can eliminate the manual processes of triaging, prioritizing, associating ownership, risk acceptance, and compliance workflows.

Achieve a Data Driven Security Program
Understand the security posture for every team with SLA compliance, MTTR, and other custom KPIs, so you can drive risk remediation and accountability across the organization.
Risk-Based Application Security Management Platform
Contextualized Data. Security Guardrails. Automated Workflows.
Tromzo is a unified platform to incorporate security throughout the modern SDLC.
Recent articles in our Blog
On a recent episode of the Future of Application Security podcast, Chad Girouard, AVP Application Security at LPL Financial, talked about some of the challenges to overcome...
Read moreOn a recent episode of the Future of Application Security podcast, Dave Ferguson, Director of Technical Product Management, Software Supply Chain Security at ReversingLabs, explained why the...
Read moreReady to Scale Your Application Security Program?
Sign up for a personalized one-on-one walkthrough.