How Tromzo Platform Works
Tromzo centralizes security data from all your security scanners in a unified security data lake, leveraging AI-powered agents to autonomously triage, prioritize, and remediate vulnerabilities that truly matter.
Discover
Centralize all your vulnerability data with Tromzo’s unified security data lake, combining code, business, and runtime context to give a complete contextual view of vulnerabilities.
Triage
AI-powered agents automatically triage vulnerabilities, assessing reachability, exploitability, and impact to prioritize real risks and eliminate noise.
Remediate
Receive tailored remediation recommendations from Tromzo’s AI agents, enabling faster, targeted fixes for high-priority vulnerabilities.
Measure
Track risk reduction with customizable, compliance-ready dashboards, demonstrating progress and aligning with your organization’s security goals.
Tromzo Platform Overview
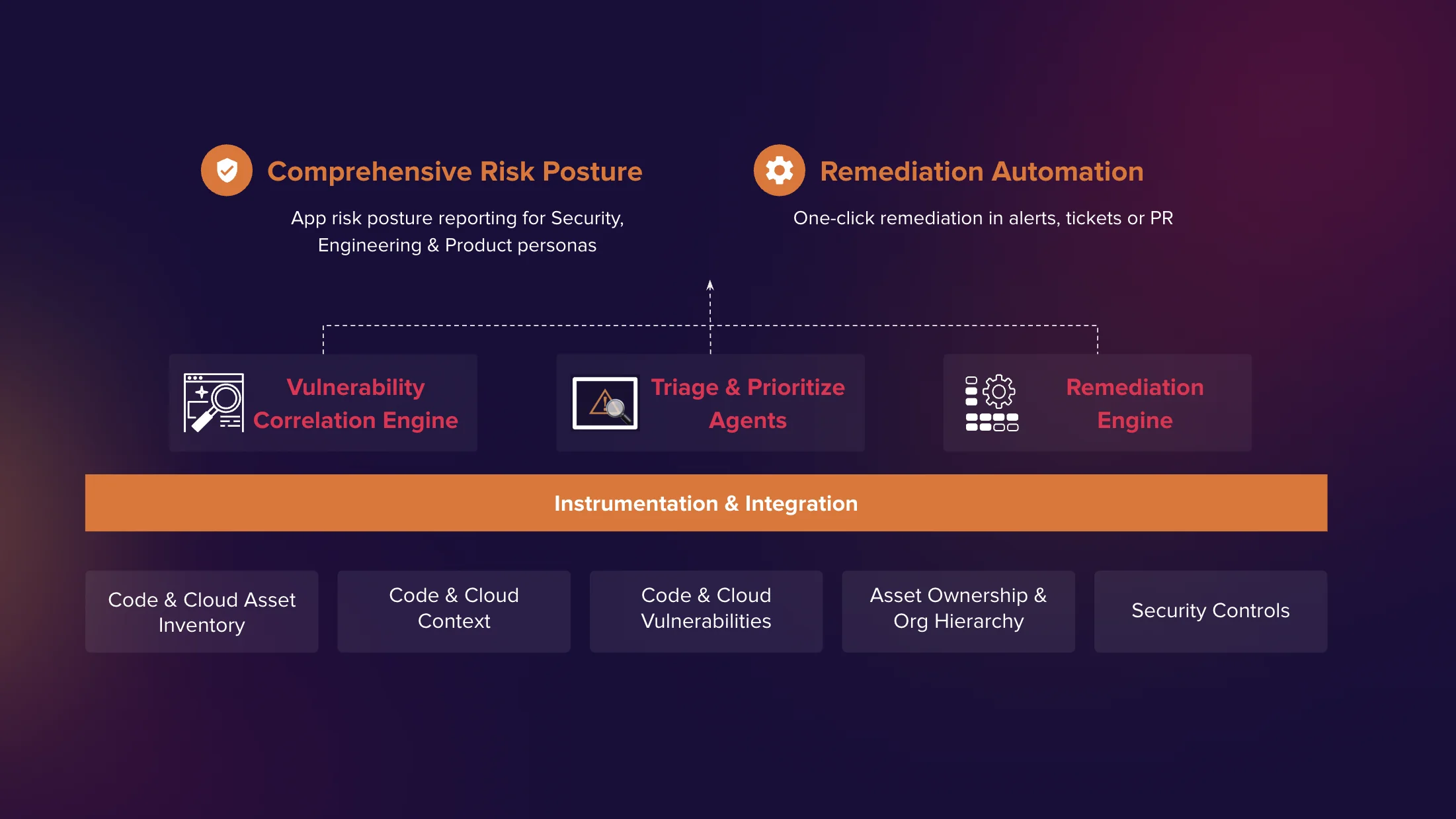
Tromzo Value
Tromzo empowers developers & product security teams to collaboratively & effortlessly build secure software, fast!
Before Tromzo
- Manual inventory of software assets
- No clear ownership data for code
- Little visibility into what is actively in production
- Multiple silos of application vulnerability and risk data
- No way of knowing what vulnerabilities should be remediated first
- Insufficient security checks in developer workflows
After Tromzo
- Centralized inventory of software assets from code to cloud
- Proper association of code to code-owners
- Run-time context to focus on what matters
- Risk-based view of all software assets with context
- Automated triaging, prioritization, and ownership
- Security policies in CI/CD to influence developer behavior
Risk-Based Application Security Management Platform
Contextualized Data. Security Guardrails. Automated Workflows.
Tromzo is a unified platform to incorporate security throughout the modern SDLC.
Security Teams That Trust Tromzo
Ready to Scale Your Application Security Program?
Sign up for a personalized one-on-one walkthrough.