Security Guardrails
Security Defined Policies, Applied in Developer Workflows
Security Guardrails are the ultimate security shift-left, enabling developers to go from code to cloud, securely. Providing tools and processes to ensure developers can build secure software by default has long been recognized as the best way to avoid security pitfalls and prevent security bugs from being introduced in the SDLC. Over the years, organizations have referred to this idea as a secure-by-default framework, security paved road, DevSecOps guardrails, and several other monikers.
Out-of-the-Box Security Controls
Leverage 100s of pre-built policies for adoption of secure defaults, safe libraries, standard images and security tool usage by developers.
Build preventative guardrails that influence developers while providing flexibility to ship software quickly.
Contextual CI/CD Policies
Customize policies based on asset context for a risk-based policy approach on critical vs. non-critical code repositories.
Flexible non-intrusive notifications in ticketing systems and the ability to build gates in CI/CD for policy enforcement.
Security Hygiene in Development
Influence developers to follow good security hygiene by introducing policy-based checks early into development process.
Implement checks to ensure clear code ownership, use of secure defaults, adoption of security tools, code scan coverage, branch protection, etc.
Measure and Report on Policies
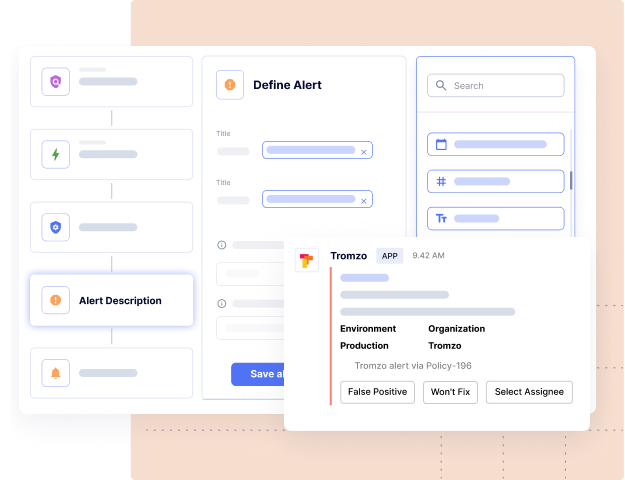
Policy violations are communicated directly to developers in real-time within their workflows.
Automated reports on policy compliance across teams and assets.
How Tromzo Can Help
Tromzo’s unified Product Security Operating Platform (PSOP) brings security visibility and control to the entire software lifecycle from code to cloud, so your organization can build secure software, fast!
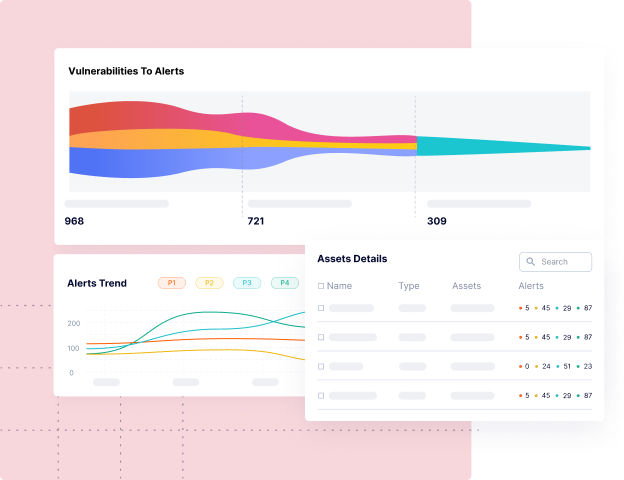

Discover Artifact Inventory & Risk Posture
Contextual software asset inventory (code repos, software dependencies, SBOMs, containers, microservices, etc.), so you know what you have, who owns them, and which ones are important to the business.
Drive Real Vulnerability Remediation at Scale
Leverage context from Intelligence Graph to tune out the noise and automate the remediation lifecycle, so you can eliminate the manual processes of triaging, prioritizing, associating ownership, risk acceptance, and compliance workflows.

Achieve a Data Driven Security Program
Understand the security posture for every team with SLA compliance, MTTR, and other custom KPIs, so you can drive risk remediation and accountability across the organization.
Risk-Based Application Security Management Platform
Contextualized Data. Security Guardrails. Automated Workflows.
Tromzo is a unified platform to incorporate security throughout the modern SDLC.
Recent articles in our Blog
On a recent episode of the Future of Application Security podcast, Chad Girouard, AVP Application Security at LPL Financial, talked about some of the challenges to overcome...
Read moreOn a recent episode of the Future of Application Security podcast, Dave Ferguson, Director of Technical Product Management, Software Supply Chain Security at ReversingLabs, explained why the...
Read moreReady to Scale Your Application Security Program?
Sign up for a personalized one-on-one walkthrough.