Risk Based Vulnerability Remediation at Scale
Traditional vulnerability management programs focus only on aggregating vulnerabilities in a centralized system and building dashboards.. While centralized reporting is important for understanding risk, the key objective of security teams is to drive risk remediation and not just report them. The only way to drive vulnerability remediation at scale today is to automate the end-to-end lifecycle of vulnerability identification, triaging, prioritization, ownership assignment, risk governance, and compliance reporting.
Aggregation & Deduplication
Integrate and standardize vulnerability data from all of your code, container, cloud, and infrastructure scanners.
Automatically deduplicate and group vulnerabilities.
Patent pending algorithm built for scaling large environments across hundreds of millions of vulnerabilities.
Contextual Prioritization
Automatically leverage business context and environmental context to prioritize the actionable few vulnerabilities that matter.
Run custom vulnerability remediation campaigns for addressing specific classes of bugs.
Reprioritize severities and group issues together based on context specific to your business.
Automated
Workflows
Automate assignment of alerts to the right individual or team within your company based on asset ownership.
Automatically create remediation tickets across one or more Jira projects, ADO boards etc. and use bi-directional sync to track remediation status at scale.
Built-in governance and approval workflows for risk acceptances, false positives, SLA, and due date extensions.
Comprehensive Dashboards
Build your own KPIs with custom visualizations to report triaged vulnerabilities and missing compliance controls.
Generate reports for every asset and team across the organization.
Gamify remediation using leaderboards with metrics like SLA compliance, MTTR, and burn down charts.
How Tromzo Can Help
Tromzo’s unified Product Security Operating Platform (PSOP) brings security visibility and control to the entire software lifecycle from code to cloud, so your organization can build secure software, fast!
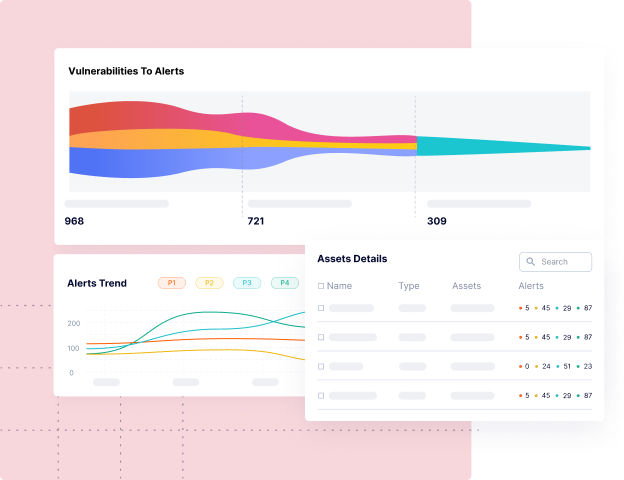

Discover Artifact Inventory & Risk Posture
Contextual software asset inventory (code repos, software dependencies, SBOMs, containers, microservices, etc.), so you know what you have, who owns them, and which ones are important to the business.
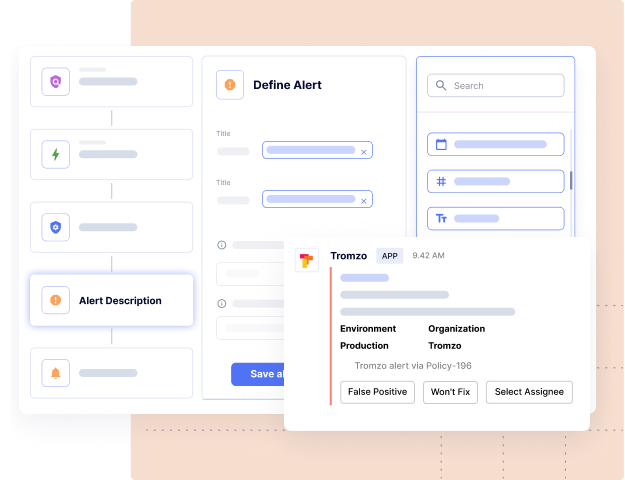
Drive Real Vulnerability Remediation at Scale
Leverage context from Intelligence Graph to tune out the noise and automate the remediation lifecycle, so you can eliminate the manual processes of triaging, prioritizing, associating ownership, risk acceptance, and compliance workflows.

Achieve a Data Driven Security Program
Understand the security posture for every team with SLA compliance, MTTR, and other custom KPIs, so you can drive risk remediation and accountability across the organization.
Risk-Based Application Security Management Platform
Contextualized Data. Security Guardrails. Automated Workflows.
Tromzo is a unified platform to incorporate security throughout the modern SDLC.
Recent articles in our Blog
On a recent episode of the Future of Application Security podcast, Chad Girouard, AVP Application Security at LPL Financial, talked about some of the challenges to overcome...
Read moreOn a recent episode of the Future of Application Security podcast, Dave Ferguson, Director of Technical Product Management, Software Supply Chain Security at ReversingLabs, explained why the...
Read moreReady to Scale Your Application Security Program?
Sign up for a personalized one-on-one walkthrough.