Legit Automated Security Guardrails for AppSec
What are Security Guardrails?
In its simplest form, security guardrails are controls that prevent deviations from expected behavior. The concept of security guardrails has existed for years in AppSec. But, it has only been attainable for a few organizations that have had very well staffed teams and a laser focus on AppSec. Teams like Netflix, Chime and Microsoft are at the forefront of creating this cultural shift.
At the core of all AppSec heartache, we find applications built with vulnerabilities and majority of these pitfalls can be avoided if we introduce security guardrails as a fundamental part of the modern SDLC.
Why do we need them?
Since legacy AppSec systems and processes historically impeded security teams and prevented them from scaling at the speed of DevOps, the need for context-specific security policies and controls that AppSec teams define and apply within developer workflows has become acute. That need is at the root of security guardrails for AppSec.
How does it work for teams not like Netflix, Chime or Microsoft?
When we launched out of Stealth in late 2021, we created the industry’s first context-aware software artifact and asset inventory with powerful workflow automation to eliminate manual processes for AppSec teams. We know a lot of vendors say “industry first”, but we truly mean it. Don’t believe us, just ask the 25+ CISOs that backed our company because they saw great potential and a true first.
Well, we have expanded on centralized visibility and workflow automation to bring another industry first when it comes to leveraging this rich context to automate controls and make real-time policy decisions across the modern SDLC.
We are thrilled that our customers have access to out-of-the-box Security Guardrails to solve for these challenges that have plagued AppSec teams for years:
- Secure Defaults – incentivize developers in CI/CD to use secure defaults in code, cloud configuration and CI/CD pipelines.
- Vulnerability Management – ensure code is being tested by the right scanners (e.g. SAST, SCA), issues are triaged automatically and important issues are resolved in a timely manner before being pushed into production.
- Code & Artifact Ownership – associate proper owners to codebases and software artifacts ensuring applications are not pushed into production without proper ownership.
- Code Change Reviews – require reviewers before merging code or automate exception workflows for code review violations.
- and plenty more we just don’t want to overwhelm you with all the awesomeness…
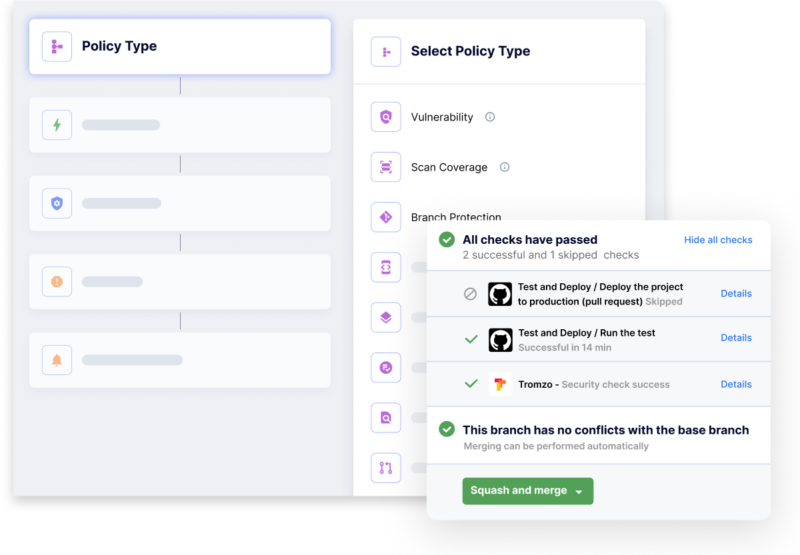
However, we know that one size doesn’t fit all, so you can easily customize existing policies or create new ones from scratch in 3 simple steps:
- Identify the policy: define what you want to be true as developers build and maintain software.
- Define the scope: not all code is created equal, so you can define differing expectations from code and artifacts that represent a higher business risk vs low risk software artifacts.
- Automate action: define the actions and notifications to be automated when these policies and controls are violated. These can be informational notifications that raise security awareness in developers, or can be more stringent gating functions in PR checks, build and deployment pipelines, etc.
We’d love to get your team up and running so your developers can start deploying secure applications.

“We built a proactive security culture as the foundation to our AppSec program, where our engineers and security team can tackle unique challenges as they build software,” said Caleb Sima, chief security officer, Robinhood. “We found the best way to influence this shift was to educate our engineers on their current security posture through implementing adoptable security guardrails.”
Upcoming LinkedIn Live
Automated Security Guardrails for AppSec
The adoption of cloud-native applications and infrastructure has propelled DevOps and a self-service culture where developers go from code-to-cloud in a matter of hours. Meanwhile legacy AppSec systems and processes have impeded security teams from being able to scale at the speed of DevOps with very little visibility or control over security risks. In this agile world, security teams are completely unprepared to govern and secure the modern SDLC.
Hear from Nir Valtman and Harshil Parikh on how organizations are leveraging security guardrails in CI/CD as the ultimate security shift-left by enabling developers to go from code-to-cloud, securely.
1:00 – 1:45 p.m. PDT on Thursday, May 19
https://www.linkedin.com/video/event/urn:li:ugcPost:6930675301832171521/
Blog Series Around Security Guardrails:
https://www.tromzo.com/blog/security-guardrails-series
TL;DR
Tromzo now provides pre-built and customizable security policies, defined by security teams and applied within developer workflows. Enabling developers to go from code-to-cloud, securely.
- LinkedIn Live – Thursday, May 19: https://www.linkedin.com/video/event/urn:li:ugcPost:6930675301832171521/
- More blogs on Security Guardrails: https://www.tromzo.com/blog/security-guardrails-series
We know there are a lot of blogs out there, so we want to say, thank you for reading ours!
Recent articles
On a recent episode of the Future of Application Security podcast, Chad Girouard, AVP Application Security at LPL Financial, talked about some of the challenges to overcome...
Read moreReady to Scale Your Application Security Program?
Sign up for a personalized one-on-one walkthrough.

