CISOs Guide to Product Security
The digital transformation has expedited product development with initiatives like agile and DevOps. With these initiatives, there has been an increase in security vulnerabilities being introduced during development. To support the organization in agile and DevOps, CISOs are adopting Product Security as the next phase in Application Security. Centralized software asset visibility, shifting left with security guardrails in CI/CD, vulnerability management automation, and analytics for cross-team accountability are the foundation to a successful Product Security program.
Recent Articles
On a recent episode of the Future of Application Security podcast, Chad Girouard, AVP Application Security at LPL Financial, talked about some of the challenges to overcome...
Read moreOn a recent episode of the Future of Application Security podcast, Dave Ferguson, Director of Technical Product Management, Software Supply Chain Security at ReversingLabs, explained why the...
Read moreOn a recent episode of the Future of Application Security podcast, Curtis Koenig, Head of Application Security at Gen, talked about how he's able to understand security...
Read moreHow Tromzo Can Help
Tromzo’s unified Product Security Operating Platform (PSOP) brings security visibility and control to the entire software lifecycle from code to cloud, so your organization can build secure software, fast!
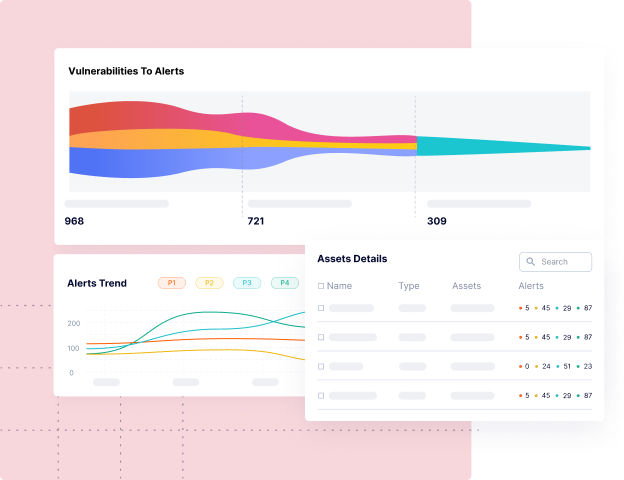

Discover Artifact Inventory & Risk Posture
Contextual software asset inventory (code repos, software dependencies, SBOMs, containers, microservices, etc.), so you know what you have, who owns them, and which ones are important to the business.
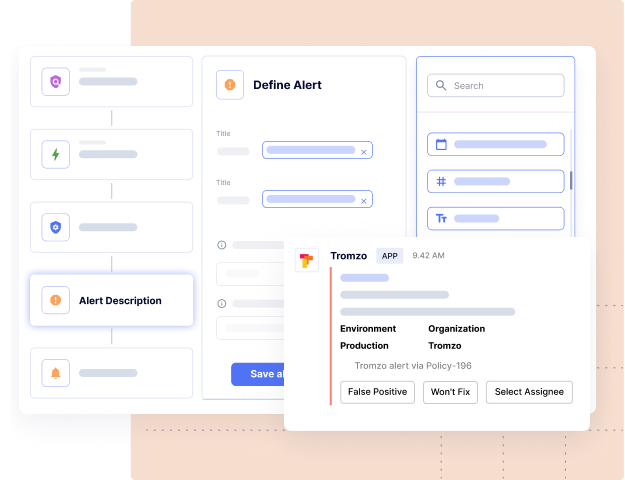
Drive Real Vulnerability Remediation at Scale
Leverage context from Intelligence Graph to tune out the noise and automate the remediation lifecycle, so you can eliminate the manual processes of triaging, prioritizing, associating ownership, risk acceptance, and compliance workflows.

Achieve a Data Driven Security Program
Understand the security posture for every team with SLA compliance, MTTR, and other custom KPIs, so you can drive risk remediation and accountability across the organization.
Ready to Scale Your Application Security Program?
Sign up for a personalized one-on-one walkthrough.